Secure Network Design: Safeguarding Digital Pathways for Enhanced Resilience
Secure Network Design is the bedrock of a tough computerized framework, giving an invigorated protection against digital dangers. In the present interconnected world, where information is an important resource, organizations should focus on the improvement of a strong organization that guarantees the classification, honesty, and accessibility of their data. We should investigate the complexities of Secure Network Design, its positive effect on hierarchical security, expected weaknesses, and the essential contemplations for building a solid computerized environment.
The Quintessence of Secure Network Design
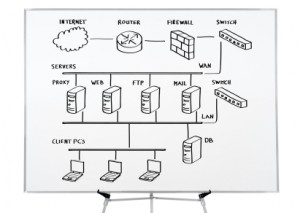
Secure Network Design includes the essential preparation and execution of organization models with an essential spotlight on shielding information and computerized resources. It envelops a huge number of components, including firewalls, interruption discovery frameworks, encryption conventions, and access controls, all functioning in a way to make an impervious stronghold against digital dangers.
Positive Effect: Invigorating Computerized Protections
Executing a Solid Organization Configuration yields various positive results for associations. Upgraded information insurance, diminished chance of digital assaults, and expanded client certainty are among the key advantages. A very much planned secure organization encourages a culture of trust among partners, advancing a positive standing and guaranteeing business progression.
Key Parts of Secure Network Design
Firewall Design
The main line of protection, firewalls screen and control approaching an active organization traffic. Appropriate arrangement is crucial for sifting through pernicious elements while permitting authentic information to stream flawlessly.
Protocols for Encryption
Data confidentiality is maintained during transmission when robust encryption is used. Secure Attachments Layer (SSL) and Transport Layer Security (TLS) are normal conventions that give a safe correspondence channel.
Interruption Discovery Frameworks (IDS):
IDS screens organization and additionally framework exercises, recognizing and making chairmen aware of potential security dangers. Early recognition is critical for moderating dangers before they heighten.
Access Controls:
Carrying out severe access controls limits client honors, decreasing the probability of unapproved access. Multifaceted confirmation adds an additional layer of safety, requiring different types of check.
Negative Impact: Vulnerabilities and Risks
Regardless of the positive angles, deficient thoughtfulness regarding Secure Network Design can open associations to extreme dangers. Shortcomings in designs, obsolete security conventions, and lacking worker preparation may prompt information breaks, reputational harm, and monetary misfortunes.
Problems with Secure Network Design
Continually Changing Threat Landscape
Digital dangers develop quickly, representing a steady test to security experts. Continuous vigilance and security measures updates are necessary to keep up with new threats.
Adjusting Security and Convenience
Finding some kind of harmony between tough safety efforts and client comfort is a never-ending challenge. Excessively prohibitive measures might hinder efficiency, while careless controls can think twice about.
Representative Mindfulness and Preparing:
Security breaches continue to be significantly influenced by human error. Absence of mindfulness and preparing among workers can incidentally open the association to weaknesses.
Key Contemplations for Secure Network Design
Risk Appraisal
Directing an exhaustive gamble evaluation distinguishes expected weaknesses and focuses on safety efforts in light of their effect and probability of event.
Normal Updates and Fix The board:
It is essential to update security systems, software, and firmware. Updates on a regular basis strengthen the overall security posture and address known vulnerabilities.
Episode Reaction Plan:
In order to lessen the impact of security incidents, it is essential to have a clearly defined plan for responding to them. Ideal and powerful reactions can forestall further harm and help in recuperation.
Future Patterns in Secure Network Design
Zero Trust Engineering:
Moving towards a Zero Trust model, where trust is rarely expected and confirmation is consistent, upgrades security by limiting the possible harm from inner and outer dangers.
Artificial Intelligence in Security:
Coordinating computerized reasoning into security frameworks empowers constant danger location, mechanized reaction, and versatile safety efforts in light of developing dangers.
Secure Access Administration Edge (SASE):
The reception of SASE joins network security capabilities with WAN abilities to help the dynamic, secure access needs of associations.
End
Secure Network Design is basic for associations trying to safely explore the computerized scene. The positive effect on information assurance and client certainty is significant, while the unfortunate results of deficient safety efforts highlight the significance of proactive procedures. By grasping the key parts, challenges, and key contemplations, organizations can sustain their advanced guards and adjust to the developing danger scene. Embracing what’s in store patterns in Secure Network Design guarantees a proactive position against digital dangers, empowering associations to flourish in an undeniably interconnected and carefully dependent world.